
Recent File Seeker is an free and portable research tool that accepts many special filters, and writes the results to a log file. The results are compatible with UVK.
Screenshot:
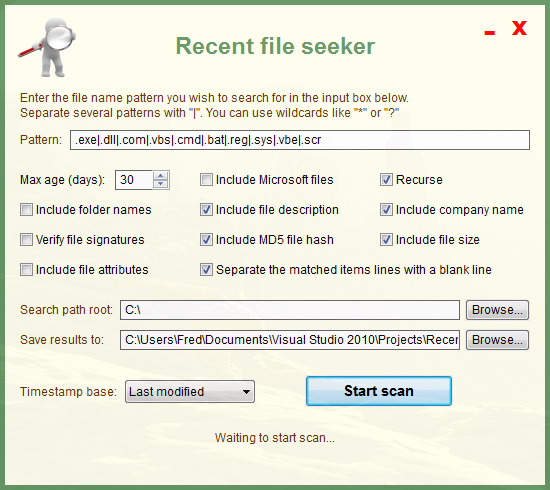
Even though RFS was created to search for malware, you can use it to search whatever you wish.
It uses a dynamic search pattern, that allows to enter several search strings at once, and also wild cards.
Setting the search pattern
Several search strings must be separated with "|". They may contain wildcards (* or ?).
The * (asterisk) will match any character zero or more times. The ? (question mark) will match any character zero or once.
The pattern is case insensitive. Example:
To search for picture files with names containing "image" in the beginning of the file name you could use the following pattern:
image*.jpg|image*.png|image*.bmp|image*.gif
Since * matches any character zero or more times, this pattern would match filenames like Image.jpg, or Image 12345.gif.
In order to restrict the same pattern to only 4 characters after "image" you could use:
image????.jpg|image????.png|image????.bmp|image????.gif
If the File name pattern field is empty, no filter will be used, so all the files created, modified or accessed (depending on which option you use) within the selected number of days will be written to the report.
A common procedure to search for malware is to use the default search pattern and set the file age field to one or two days before the infection. RFS will then search all the executable files, DLLs, cmd and vbs scripts, and drivers modified within the selected number of days.
Choosing the path for the log and the timestamp base
The results will be saved to the file in the field Save results to:. Use the Browse button in the same line to select a different file.
You can choose to search the files/folders based on their creation date, last access or last modified, in the Timestamp base combo box.
Writing the information to the log
The information corresponding to a matched file will make one line in the log. The format is as follows:
Mode | Last write time | Path | File attributes | File description | File size | MD5 hash | Publisher name
As you can see, the information will be written in several fields separated by " | ", just like in the UVK log.
Not all the fields above may be present. That will depend on the options you select before starting the scan. These options are pretty much self-explanatory, but we will explain them anyway:
Mode : (<RecentFiles>) This keyword is always present. It is used by UVK as reference, in case you wish to delete the corresponding file using UVK.
Last write time : This field is always present. It may also be the creation time, or the last access time, depending on which option is selected in the Timestamp base combo box.
Path : The matched file object's full path. This field is always present.
File attributes : The matched file object's attributes.
It's a string in the format "RASHNDOCT". Each letter of the string
will be present if the corresponding attributes are set:
"R" =
READONLY
"A" = ARCHIVE
"S" = SYSTEM
"H" = HIDDEN
"N" = NORMAL
"D" = DIRECTORY
"O" = OFFLINE
"C" = COMPRESSED (NTFS compression,
not ZIP compression)
"T" = TEMPORARY.
This field will be present if the Include file attributes checbox is checked.
File description : The matched file object's description. This field will be present if the Include file description checbox is checked.
File size : The matched file object's size. This field will be present if the Include file size checbox is checked.MD5 hash : The matched file object's MD5 hash. This field will be present if the Include file MD5 hash checbox is checked.
Please note that the file hash generation requires reading the entire file, which can take long for big files with one or more GB.
Publisher name : The matched file object's publisher's name. This field will be present if the Include company name checbox is checked.
If Verify file signature is checked, the publisher will be verified, allowing you to check the authenticity of the file.
Check Include Microsoft files if you want all the files matching the pattern to be shown. Leaving this box un-checked will make RFS ignore Microsoft files.
Un-check Recurse if you don't want RFS to recurse sub-directories. This will make RFS only report files within the selected folder.
Check Include folder names if you want RFS to search the pattern in folder names too. In this case, if you use file extension patterns for the file names you should add one or more patterns for the folder names.
e.g: if you want to search for executable files, drivers and folder names containing Antivirus XP you should use the pattern .exe|.sys|antivirus xp*.
Performing the scan
You can choose the root folder or drive for the scan, by clicking the Browse button in the Search path root line, or manually entering the path in the corresponding input box.
When the desired options are set, you can click the Start scan button, or press the Enter key to start the scan.
Wait while RFS scans the selected folder or drive for files matching the desired features.
You can stop/pause the scan anytime by clicking the same button, which has been renamed Stop scan.
Download
Click the button below to download the latest version of the tool:
Current version:
What's new in this version
The application was completely rewritten in C++. Previous versions were coded in AutoIt.
Added the Include file attributes, Include file size, Include MD5 hash, Verify file signatures, and the Double line break in the report features.
Automatic detction of UVK installation in order to open the log with the UVK's log analyzer if possible.
